How to create a VPC (and delete it)
AWS VPC is something you must have before you can start building services on AWS. In theory you can do some serverless applications using Lambda, S3 and DynamoDB, and be deployed without a VPC but pretty soon you will want to deploy other things that must go into a VPC.
Brief history
In the early days of AWS there was no VPC but EC2 (classic) and all other services were deployed into AWS managed networks with public IPs (so you could connect to them). While this model came with huge limitations it also made getting started very simple as you didn’t have to worry about network design because you had no control over it.
EC2-Classic has been deprecated since 2013 (!) and as I’m writing this (August 2022) the very last of classic instances are getting terminated.
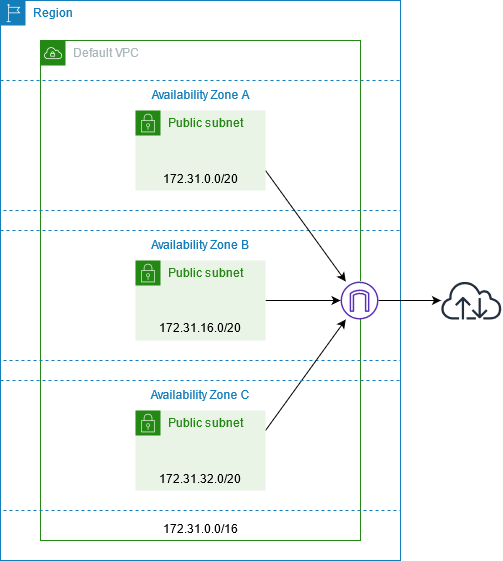
When VPC was introduced every account (and region) got a default VPC. It was to bridge user experience from not having to design a network before deploying the first VM to new VPC based model where you must have VPC first before you can deploy anything. While default VPC did make it very simple to get started, it was no good for building anything beyond that first VM. If you ever did make a mistake of building non-trivial architectures into default VPC you quickly hit the dead-end and to fix your network architecture you had rebuild most of your services from scratch :-(
Creating your own VPC …
AWS console’s “New VPC Experience” has now GUI to create VPCs. It lets you specify VPC CIDR, number of AZs, whether there is going to be public and/or private subnets, and NAT gateways. In short this lets you create VPCs that are much more usable than default VPC.
When you have defined how you want to have your VPC, there is preview of all resources that are going to be created next. This is nice eye candy but it would be even more usable if preview would look similar to how VPCs are presented in AWS documentation. Maybe even having an option for exporting to diagraming tools like Lucidchart and Draw.io?
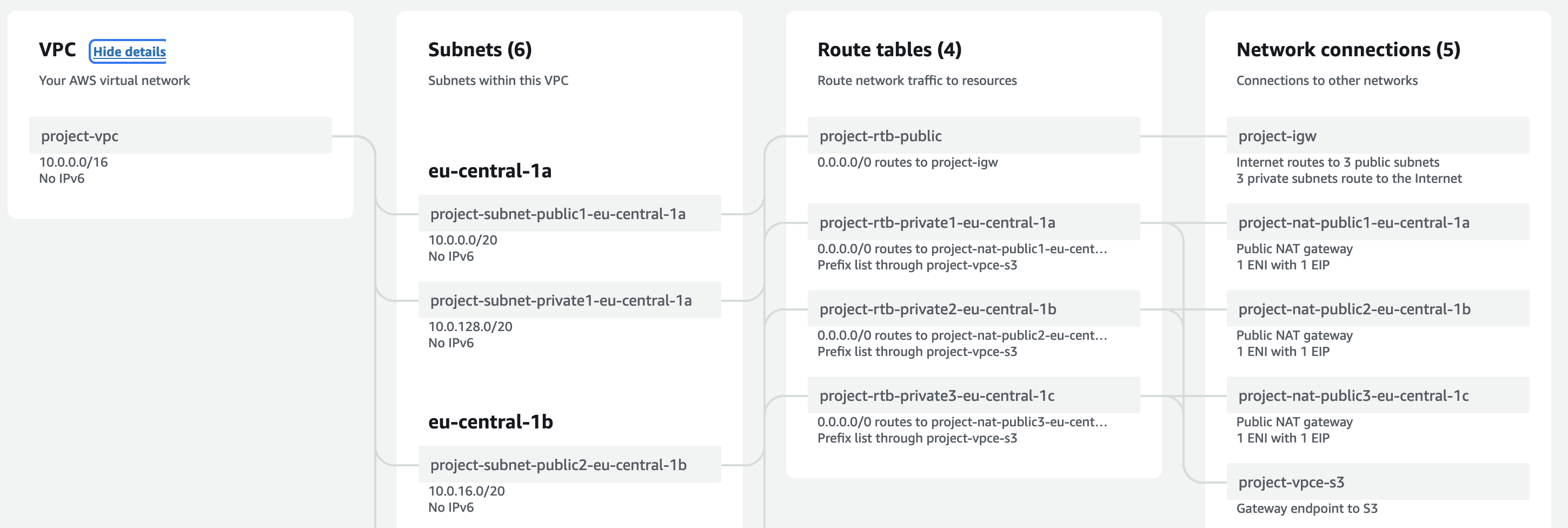
And when you’re happy with design, click “Create” -button and watch how VPC is getting build!
… And deleting it
Creating a new VPC was easy, how about deleting one when you don’t need it any longer? There is “Delete VPC” action that sounds like it should take care of it.
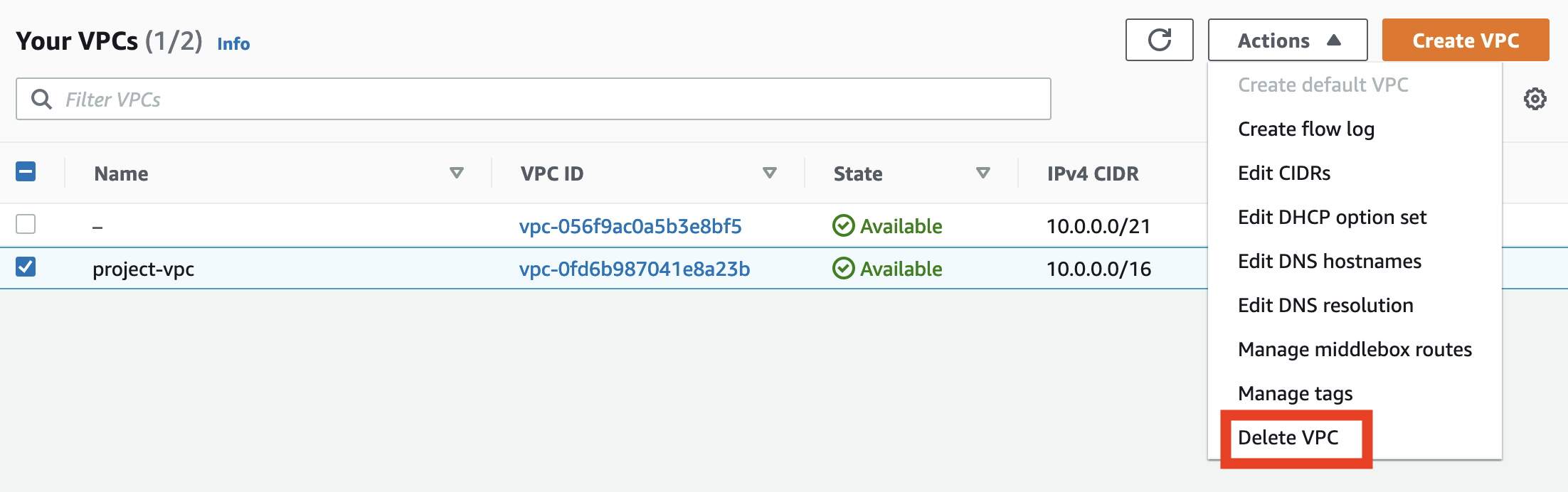
To delete VPC you must first deprovision all services from it. But even if you cleaned what you created, or try to delete VPC right after you created it, it might not work but complain network interfaces are still in use and there are NAT gateways deployed into VPC. If you didn’t include NATs in VPC, then delete should work fine.
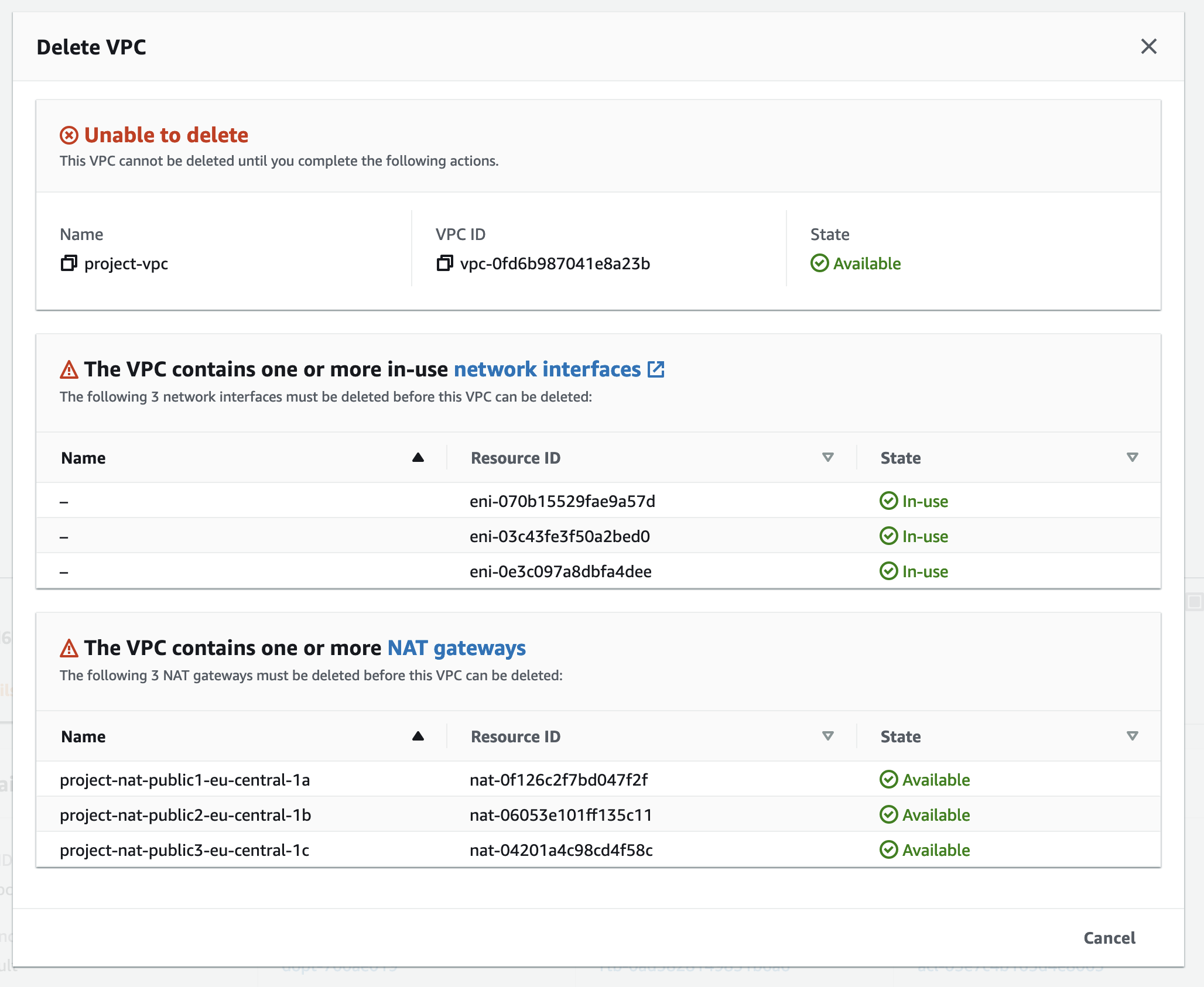
If you try to delete network interfaces, that won’t work. This is because interfaces are attached to NAT gateways, and NAT is AWS managed service so you can not go and modify it’s resources directly. Error message would be more informative if it would report network interfaces being part of NAT gateways and ask you just to delete NAT’s as that would take care of interfaces too.
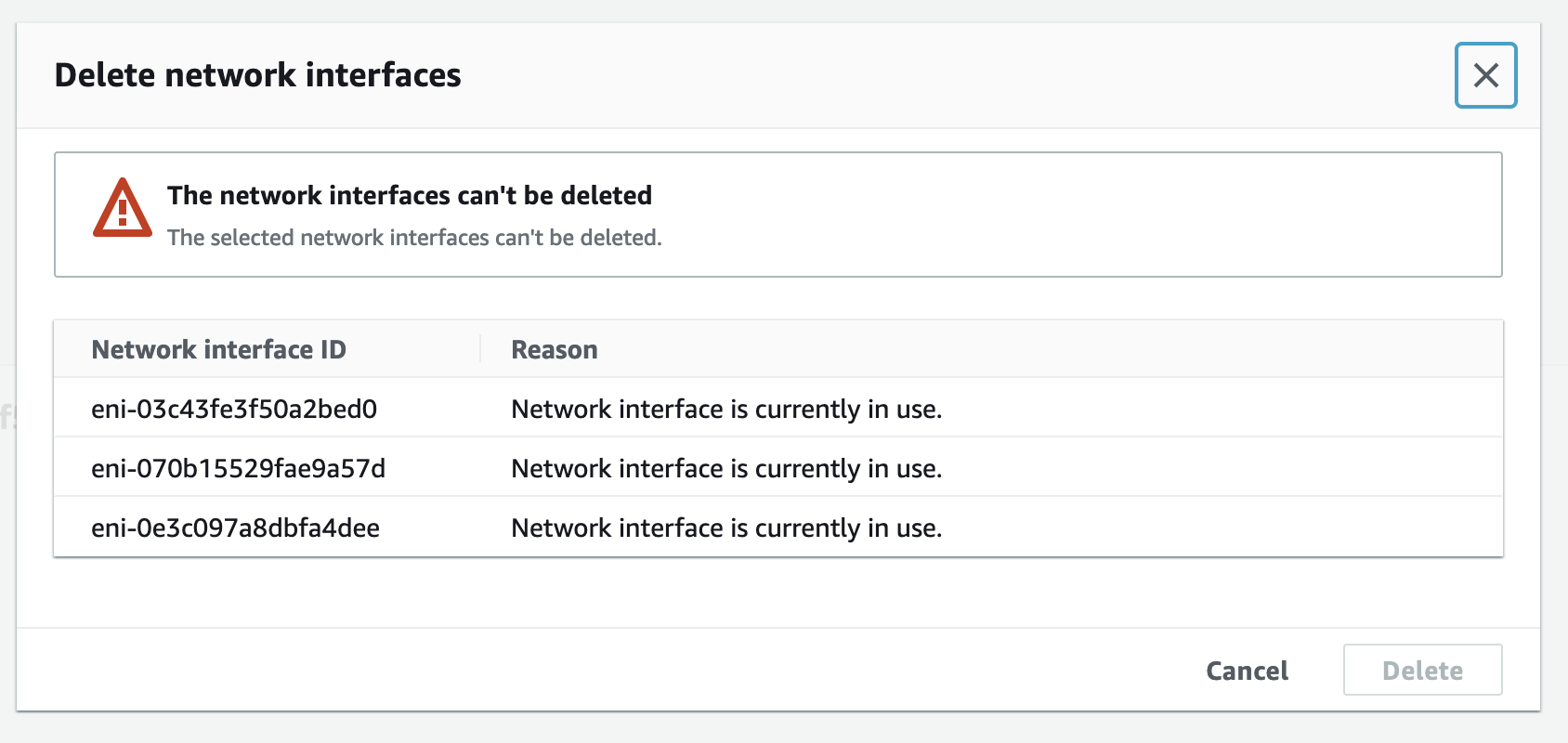
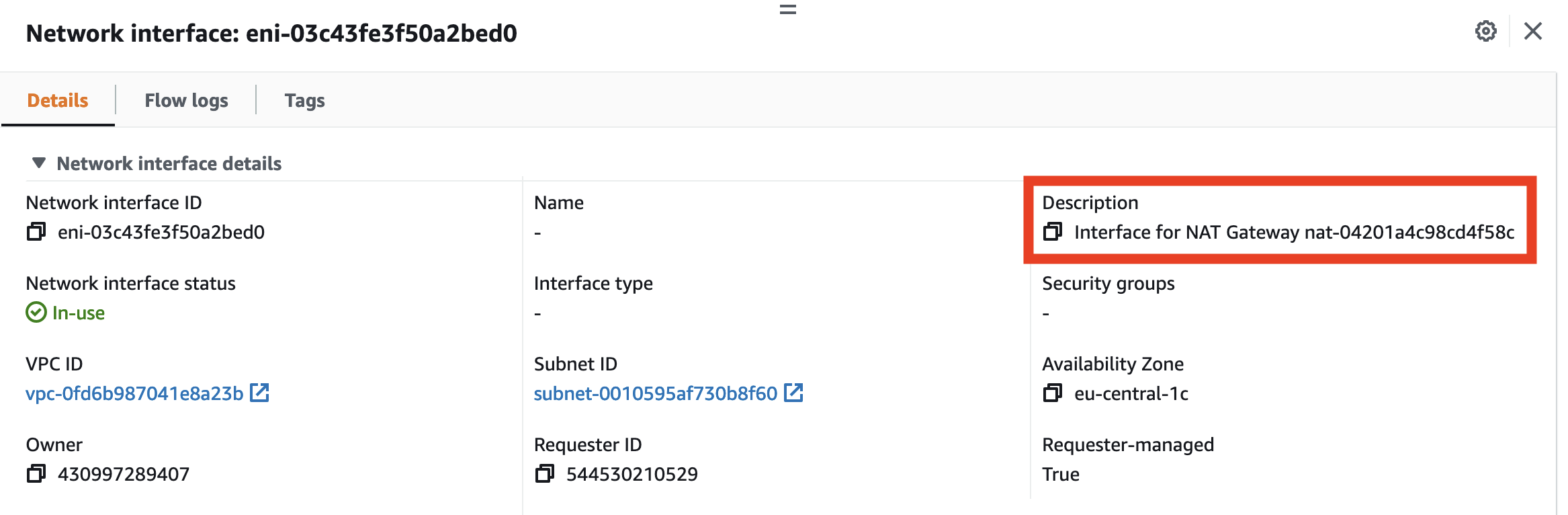
Connection between ENIs and NAT gateways is found from ENI details.
When “Delete VPC” has run successfully you should have cleaned up everything? Almost, but there can still be Elastic IPs left from NAT gateways. You should relese EIPs that are no longer in use because having them unattached incurs some costs, and there is a limit how many EIPs you can have per region. By default the limit is 5 EIPs, so if you forget to release them, you are likely to hit the limit when you try to create next VPC.
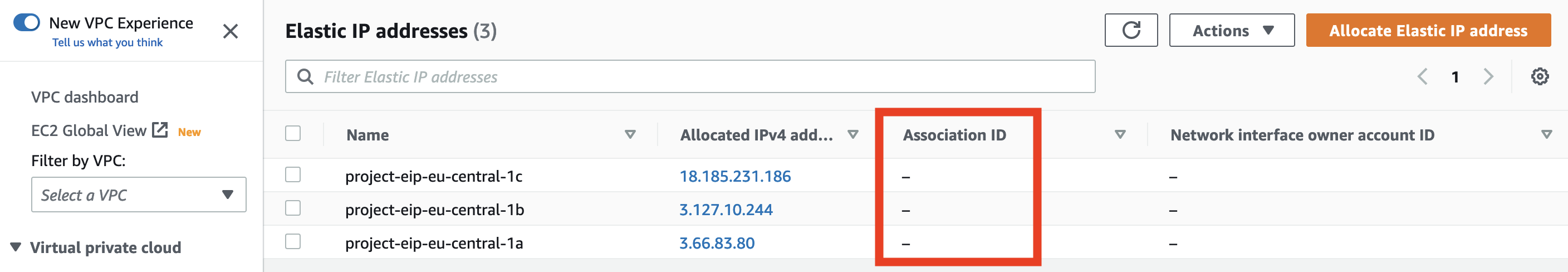
Now you have finally deleted VPC and all resources created with it.
Summary
New VPC creation UX in AWS console is big step forward when compared to default VPC. GUI wizard makes it much easier, for beginners and people who are not that interested in fine details of AWS networks, to create standard VPCs.
To make it even more usefull …
-
Preview could include network diagram -view of VPC. Current version feels like eye candy with very little value for real world use-cases.
-
There should be also “Delete VPC” wizard. Creating is now made easy for beginners, but cleaning up what you created requires some experience with AWS network services.
-
Using Cloudformation to deploy VPC. This would solve “Delete VPC” problem but also allow user to modify settings after VPC is created, e.g. adding adding NAT gateways or private subnets, if the initial plans were changed.
Ps. If you got interested in VPC design, I wrote a post about deploying VPCs that can be later modified for different requirements. I’ve also published Cloudformation template that implements ideas presented in the post.